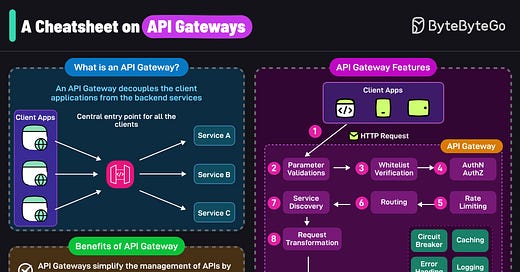
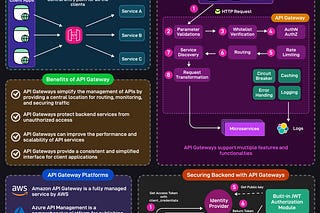
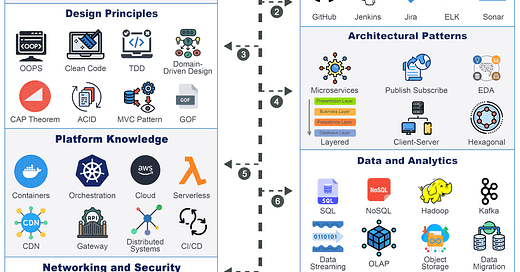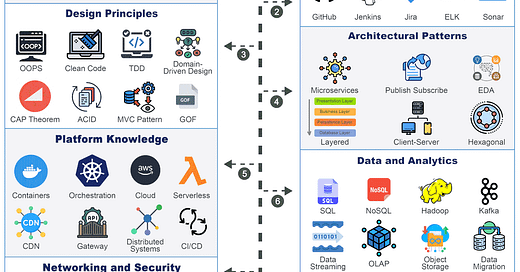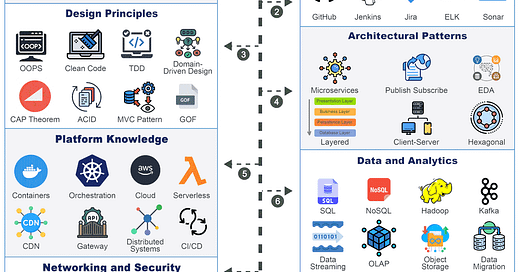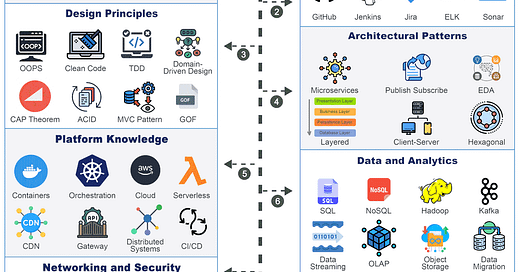
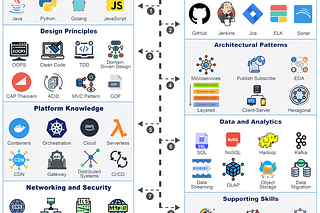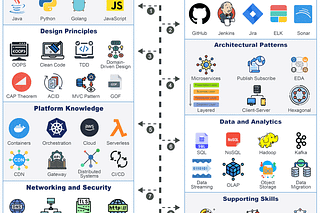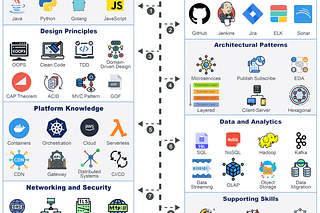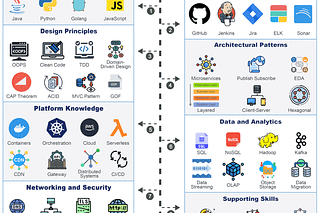
In today's rapidly evolving digital landscape, developers face the constant challenge of building applications that are not only robust and secure but also infinitely scalable.
At the heart of this challenge lies a fundamental architectural decision: how to handle the application state. The state is your application's memory—every user session, shopping cart, and authentication token that makes personalized digital experiences possible.
The journey from stateful to stateless architectures represents one of the most important shifts in modern system design.
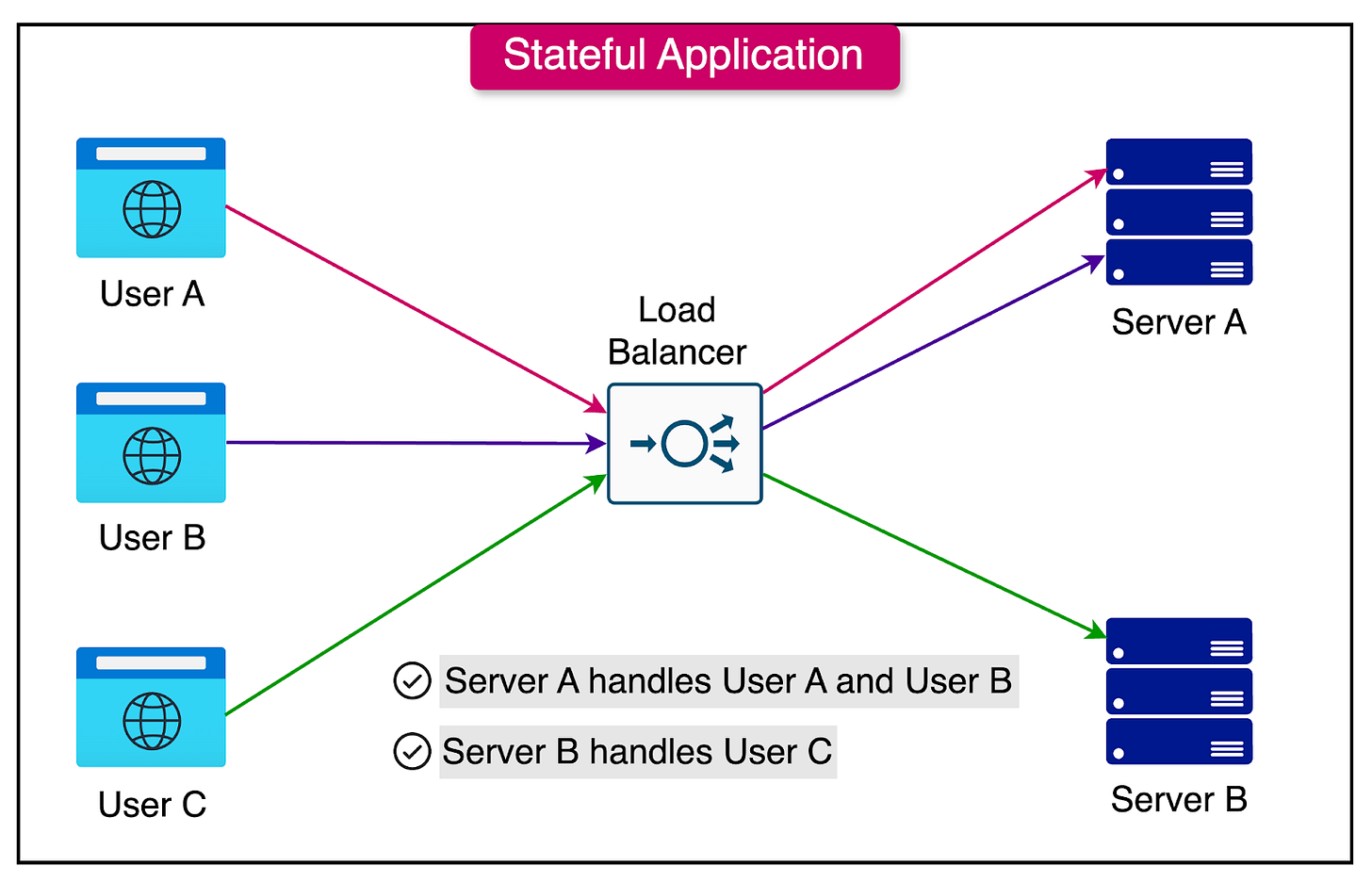
Traditional stateful applications dominated the early 2000s and directly maintained user sessions and data on application servers. While this approach of keeping everything in one place seemed logical initially, it created significant challenges as applications scaled to serve millions of users worldwide.
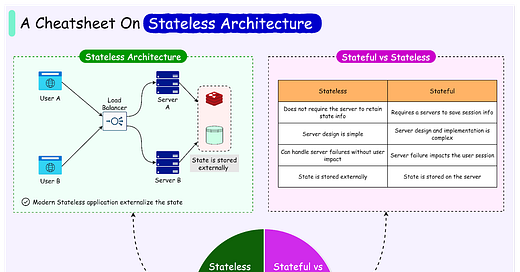
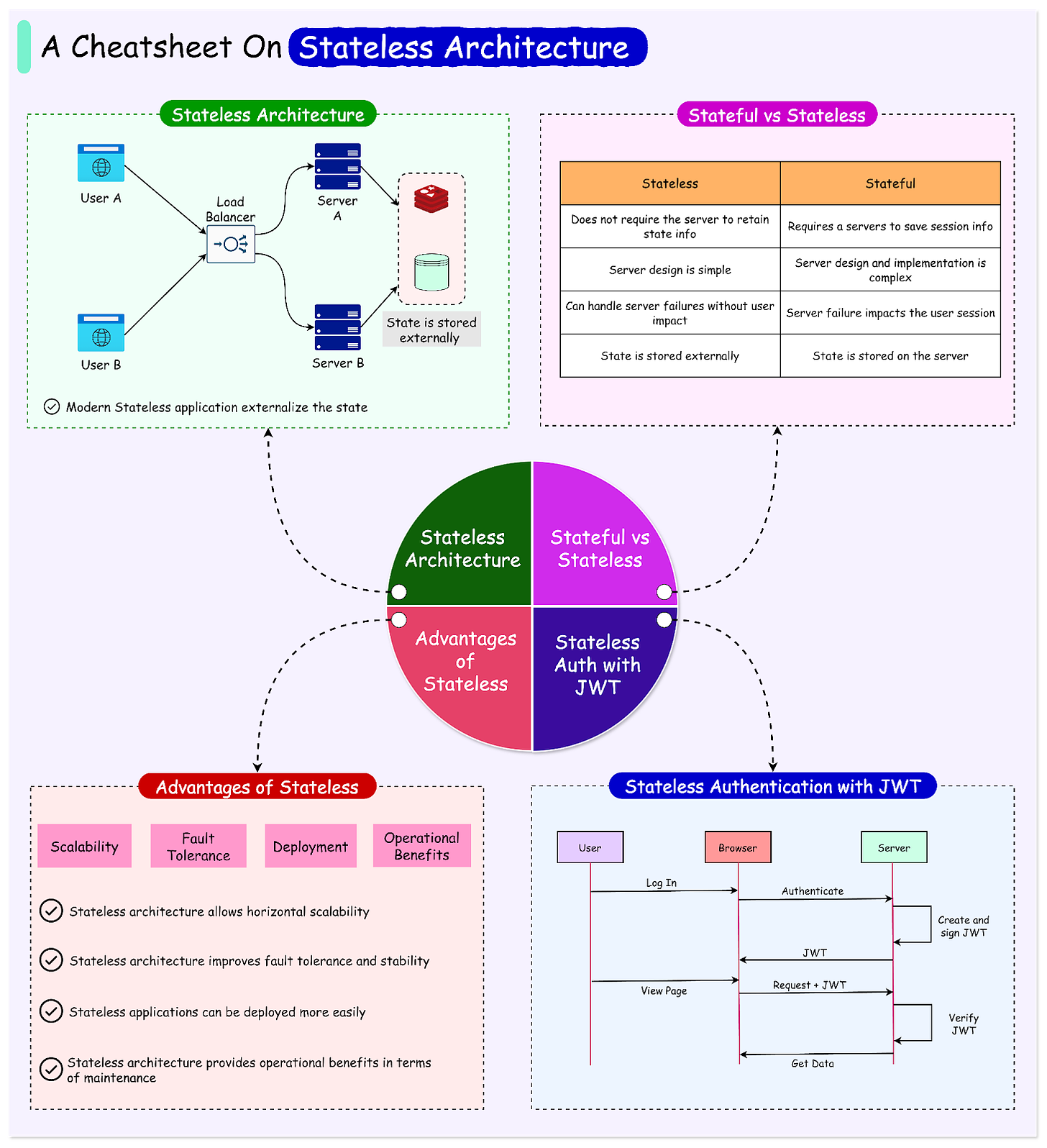
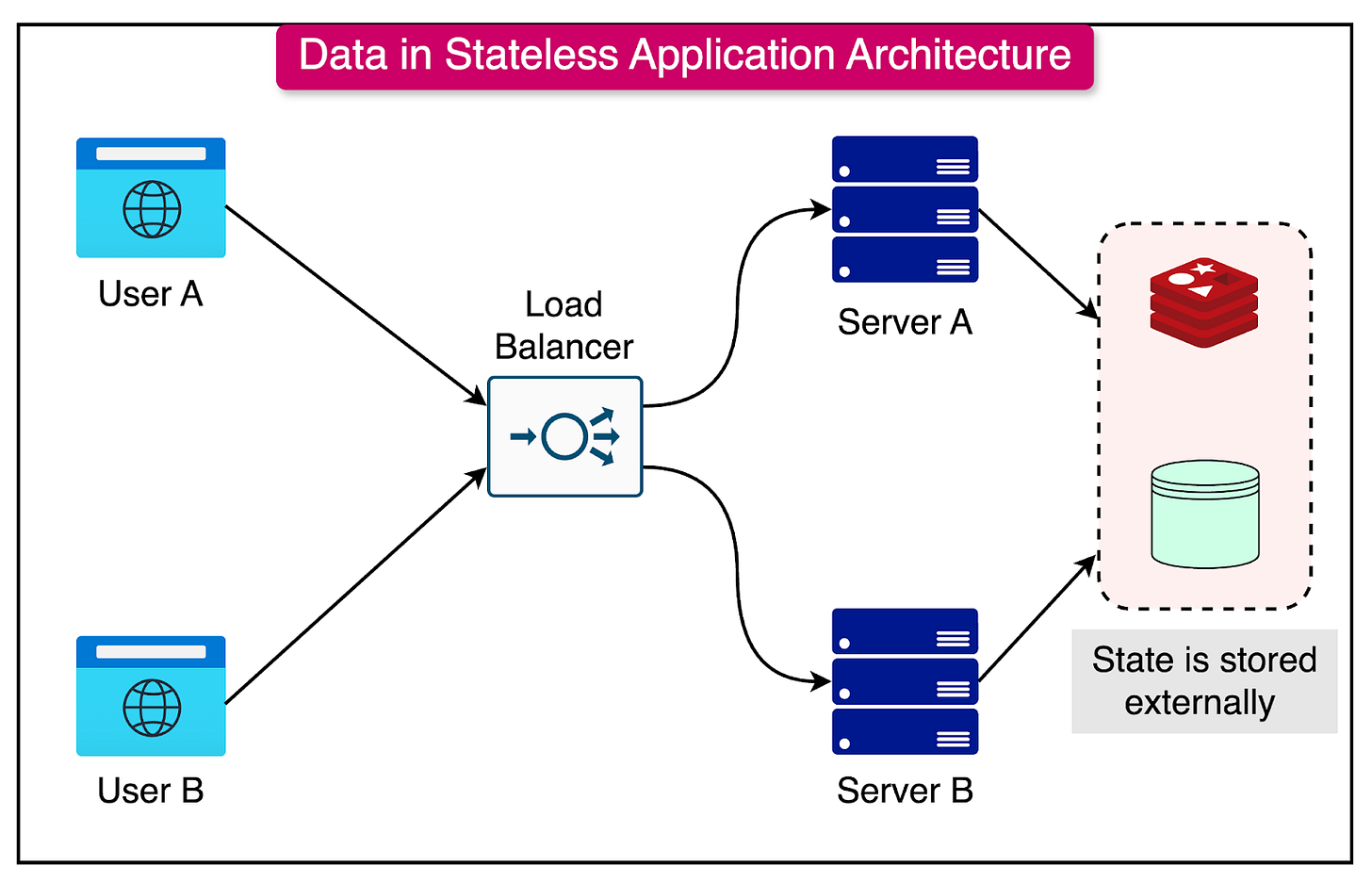
Consider an e-commerce platform handling Black Friday sales. In a stateful architecture, each server will need to maintain session information for thousands of users, leading to complex load-balancing requirements and potential session loss if a server fails. Modern stateless architectures, however, externalize this state, allowing any server to handle any request, dramatically simplifying scaling and improving reliability.
Several converging factors have led to the industry’s embrace of stateless architecture:
The rise of cloud computing has made horizontal scaling not just possible but economically advantageous.
The shift from SOAP-based services to REST and GraphQL APIs, which are inherently stateless.
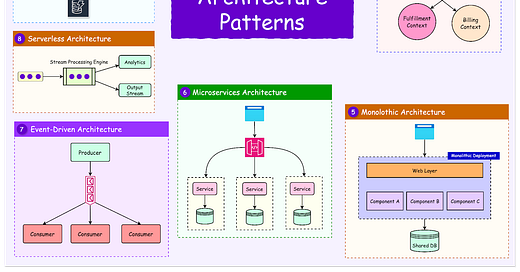
Microservices architectures, which break down monolithic applications into smaller, independent services, have become the norm rather than the exception. These services must be stateless to maintain independence and scalability.
In this article, we’ll explore the principles, implementation strategies, and best practices of stateless architecture.
What is Stateless Architecture
Stateless architecture represents a fundamental shift in how modern applications handle data and user interactions. Unlike traditional stateful systems, stateless services don't maintain any server-side state between requests, creating more flexible and scalable applications.
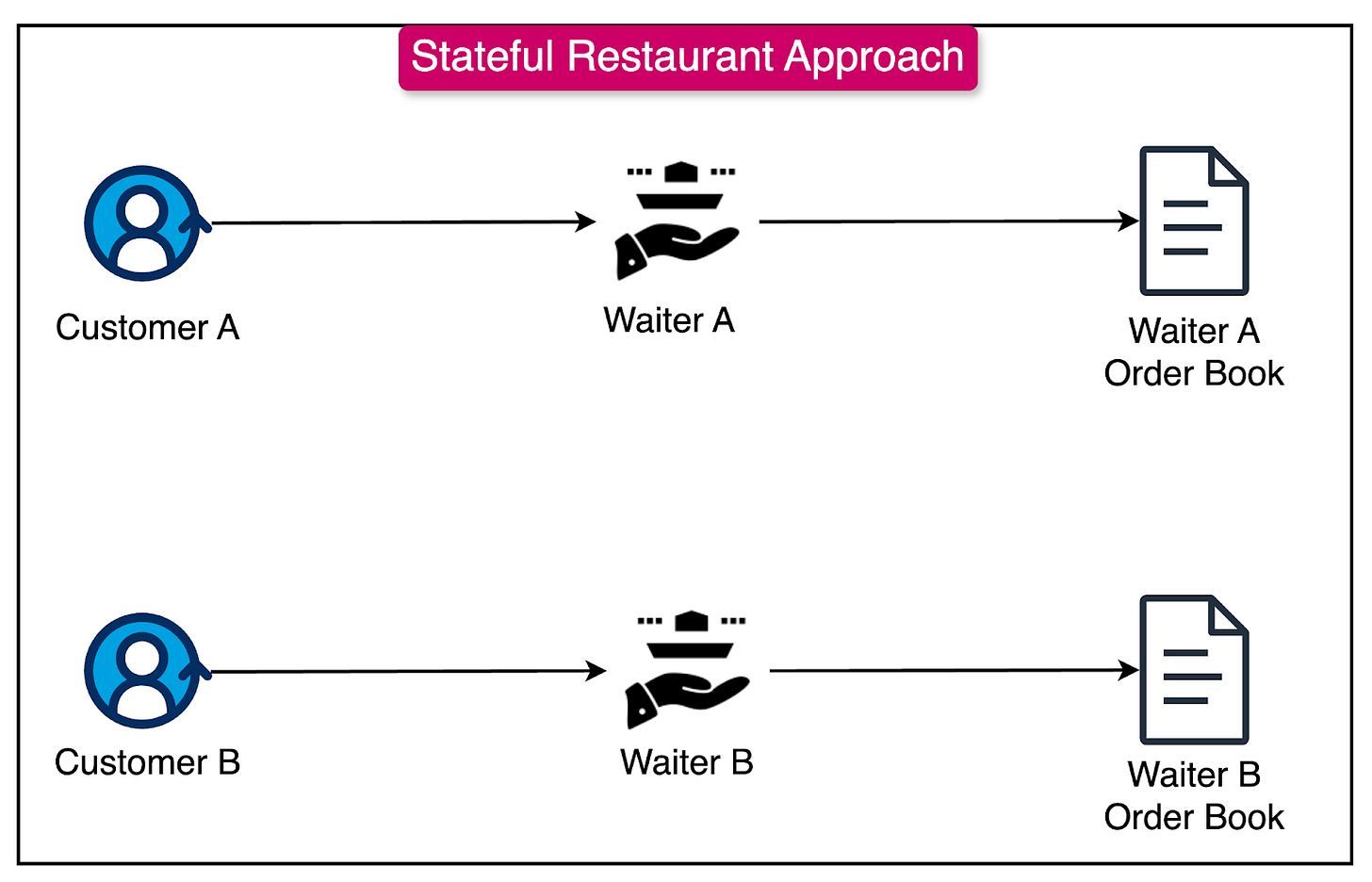
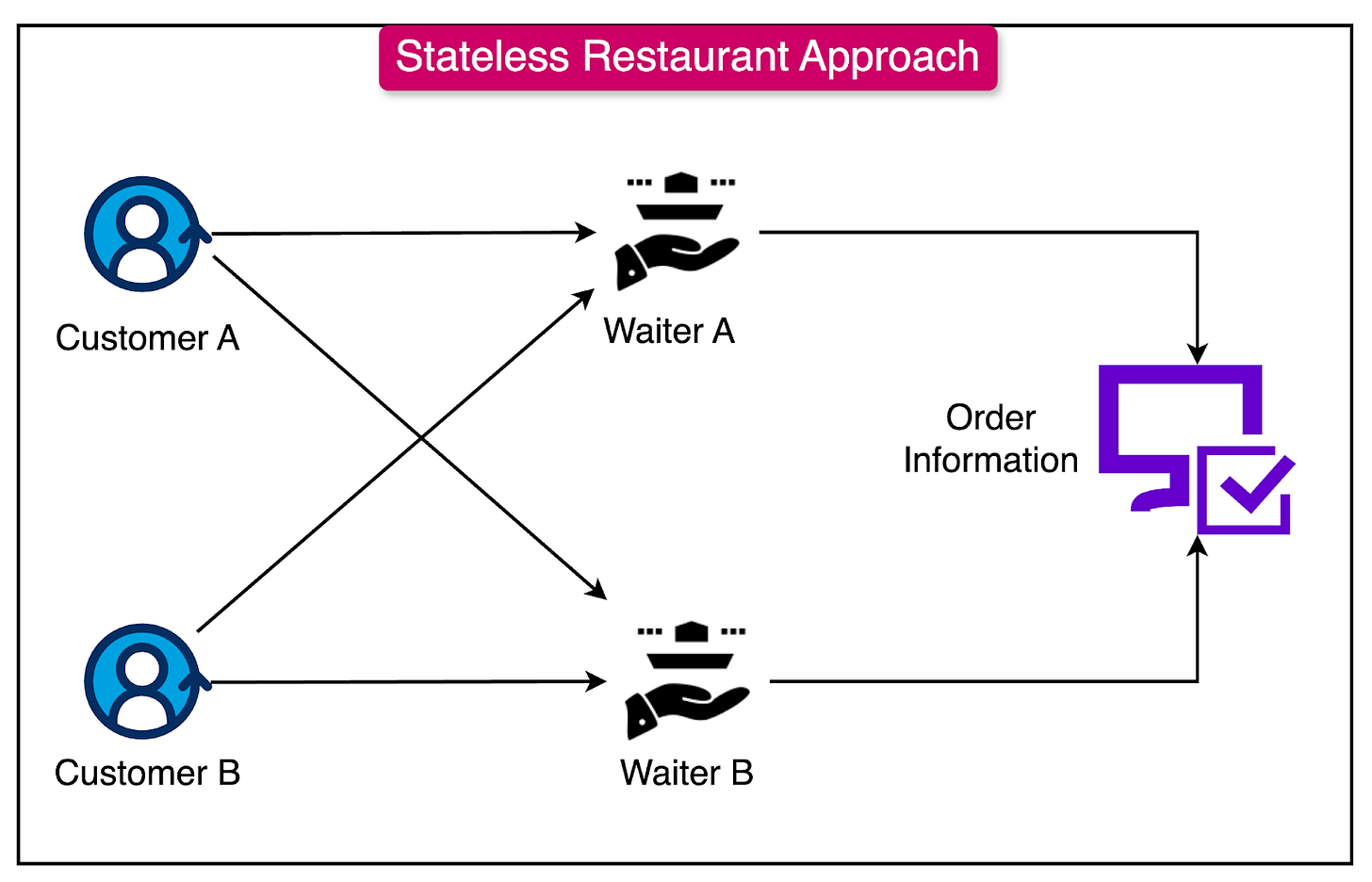
To understand stateless architecture, consider a restaurant scenario:
Stateful vs Stateless Approach
In a stateful approach, you'd have one dedicated waiter who keeps your entire order information in their notepad. If this waiter becomes unavailable, other waiters have no context about your order—much like a server maintaining specific user sessions.
In contrast, a stateless approach is like having all waiters share a centralized system for order information, where any waiter can handle your request by accessing the central system.
The technical implementation of stateless architecture requires each request to be self-contained and include all necessary information for processing. Instead of storing session data in server memory, stateless systems utilize external databases or caches.
User authentication is handled through tokens rather than server sessions, and important data like shopping cart contents are stored in distributed databases accessible to all servers.
Core Principles of Stateless Design
The foundation of stateless architecture rests on several key principles that ensure the scalability, reliability, and maintainability of modern distributed systems:
Separation of State from Application Logic: In a stateless design, application servers function as pure computational units, processing requests without maintaining client context.
Request Independency and Idempotency: Each request in a stateless system must be self-contained and capable of being processed independently. It is important to design idempotent APIs to ensure that multiple identical requests produce the same result.
Data Consistency Models: Stateless architectures require careful consideration of data consistency patterns. For example, implementing eventual consistency models for distributed state storage. Also, there is a need for centralized storage systems that are accessible to all service instances.
The Advantages of Stateless Architecture
The stateless architectural approach offers several advantages related to scalability, reliability, deployment flexibility, and operational efficiency.
Let's explore these advantages through practical examples and real-world scenarios.
Horizontal Scalability
One of the primary benefits of stateless architecture is the ability to scale horizontally with ease.
Traditional Stateful Approach:
Each server maintains specific user sessions.
Load balancers must use sticky sessions to route every request by a particular user to the same server.
New servers can't effectively share the load since users are bound to specific servers.
Stateless Solution:
Any server can handle any request.
State information is stored in distributed databases or caches like Redis.
New servers can be added seamlessly to handle increased traffic.
The stateless approach enables the system to scale dynamically by adding or removing servers based on demand, without the constraints of user session affinity.
Fault Tolerance and Reliability
Stateless architecture significantly improves system reliability. For example, going back to the example of a stateful restaurant, if a waiter leaves during their shift, all the customers' order information goes with them.
Similarly, in stateful applications, if a server fails, all user sessions on that server are lost. Users might suddenly find themselves logged out or lose their shopping cart data.
In contrast, the stateless design ensures:
No single point of failure for user sessions
Seamless failover to other servers
Consistent user experience even during partial system failures
By decoupling state from individual servers, stateless architecture enhances fault tolerance and ensures uninterrupted service even in the face of server failures.
Deployment Flexibility
Stateless services make deployments a lot easier to manage:
Rolling Updates: Stateless services can be updated without service disruptions, as new versions can be deployed incrementally across the server fleet.
Container Orchestration: Stateless services are well-suited for containerization and orchestration platforms like Kubernetes, enabling efficient deployment and management.
Cloud Compatibility: Stateless architecture aligns well with modern cloud infrastructure, allowing for seamless integration with cloud-native services and auto-scaling capabilities.
The deployment flexibility of stateless services simplifies the process of releasing new features, applying patches, and managing the application lifecycle.
Maintenance and Operations
The separation of state from application logic provides operational benefits:
Debugging and Troubleshooting: Stateless services are easier to debug and troubleshoot, as each request can be treated independently without the need to track complex state interactions.
Server Maintenance: Stateless servers can be easily replaced or upgraded without impacting the overall system, as they do not hold critical state information.
Predictable Scaling: Stateless architecture enables more predictable scaling behavior, as the system can be scaled based on well-defined metrics and resource utilization patterns.
Resource Utilization: Stateless services can be efficiently distributed across available resources, leading to better overall system utilization and cost optimization.
Architectural Components of Stateless Design
Stateless architectures require careful consideration of state management and communication patterns to ensure system integrity and scalability.
State Management
In stateless architectures, state management is decentralized from application servers, necessitating thoughtful approaches to storage and access patterns:
External State Storage:
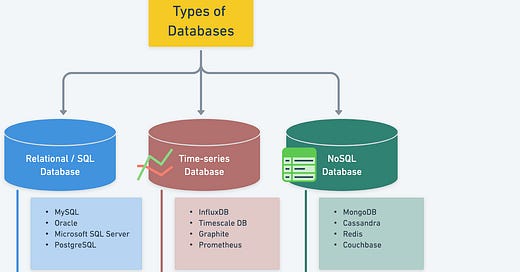
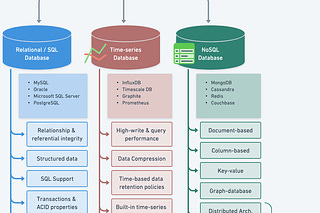
Structured data is stored in relational databases for ACID-compliant transactions.
Unstructured data utilizes NoSQL databases and key-value stores for flexibility.
Large objects and files are managed through specialized storage solutions like Amazon S3.
Caching Strategies:
Distributed caches like Redis serve as high-performance state stores.
Session data and authentication tokens are cached for quick access.
Multi-layer caching implements both local and distributed caching patterns.
Data Synchronization:
State changes are replicated across multiple storage instances.
Eventual consistency models handle distributed state updates.
Conflict resolution mechanisms manage concurrent modifications.
Communication Patterns
Modern stateless architectures employ various communication patterns to maintain system integrity and scalability:
RESTful Implementation:
APIs are designed to be idempotent and stateless.
Each request contains all the necessary context for processing.
Resources are manipulated through standard HTTP methods.
Event-Driven Architecture:
Services communicate through events rather than direct calls.
Message queues handle asynchronous state updates.
Pub/sub patterns enable loose coupling between components.
These communication patterns promote loose coupling, scalability, and fault tolerance in stateless architectures.
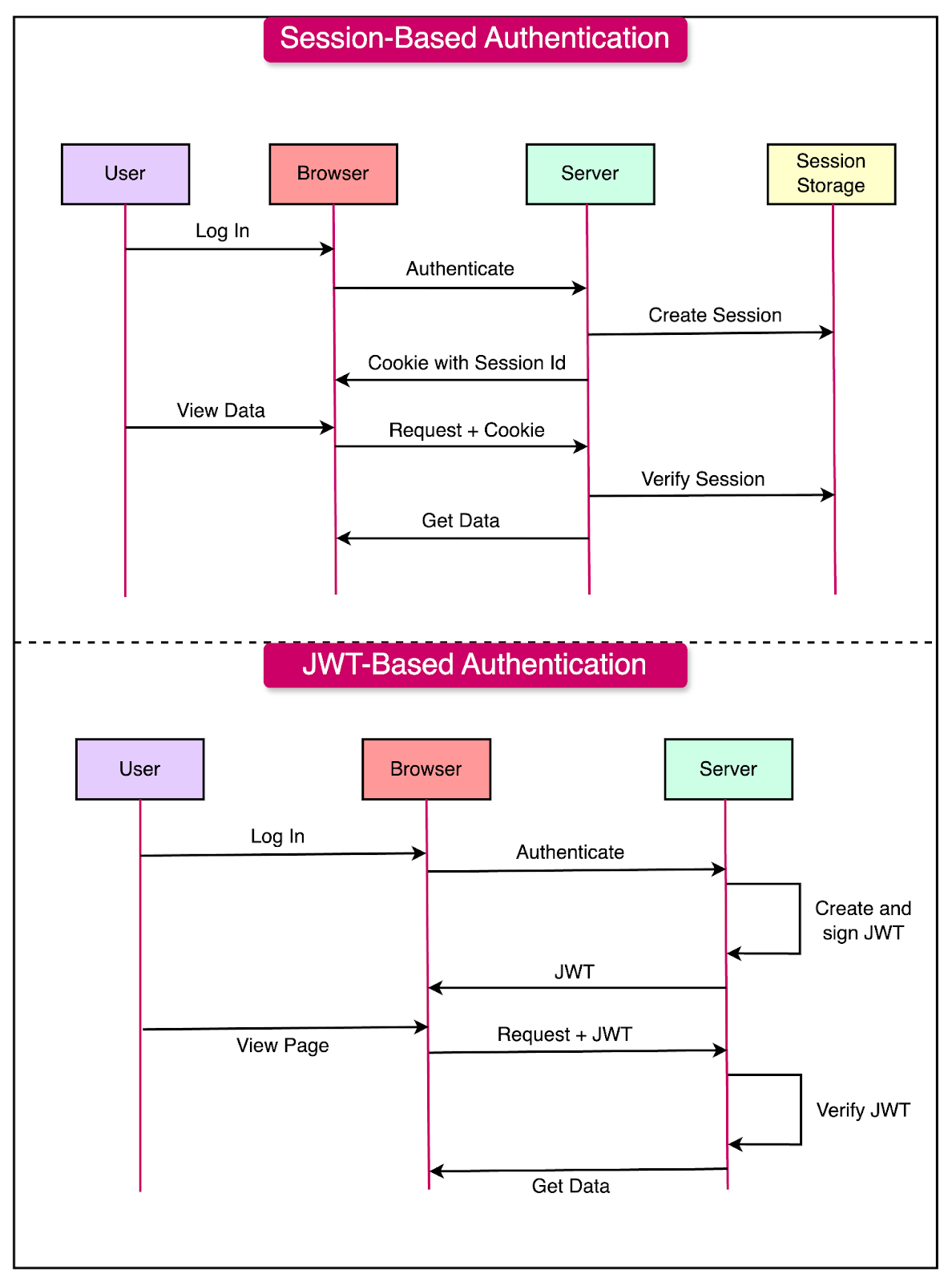
Authentication Flow
In stateless architectures, authentication flows are designed to be token-based rather than session-based:
Token-Based Authentication:
JWTs (JSON Web Tokens) carry user context and claims between services.
Cryptographically signed tokens ensure security and integrity.
Tokens are stateless and can be validated by any service.
Stateless Sessions:
Session data is stored in distributed caches or databases.
Services retrieve session information from the shared storage as needed.
Stateless sessions enable horizontal scalability and fault tolerance.
By adopting stateless sessions and token-based authentication, stateless architectures provide secure and scalable user authentication and authorization.
Migration Strategies: Transitioning to Stateless Architecture
Starting with a stateless application from scratch is easy. However, moving from an existing stateful to stateless architecture requires careful planning and execution to ensure a smooth transition while maintaining business continuity.
Incremental Transition
The journey to stateless architecture is best approached through gradual transformation rather than a complete overhaul. An incremental transition involves the following steps:
Phase-Based Migration:
Start with non-critical services that have minimal dependencies.
Gradually move user-facing components while maintaining backward compatibility.
Implement new features using stateless patterns while maintaining existing stateful systems.
Hybrid Architecture Patterns:
During the transition, organizations often need to maintain stateful and stateless components.
Use API gateways to route traffic between old and new systems.
Implement facade services that abstract the complexity of dealing with both architectures.
Maintain a shared state store that both stateful and stateless services can access.
This incremental approach allows for a controlled and manageable transition, minimizing disruption to existing systems.
Legacy System Integration
Integrating existing systems into the new stateless architecture requires careful consideration of dependencies and compatibility:
Integration Strategies:
Implement adapter services to translate between stateful and stateless components.
Use event-driven patterns to decouple legacy systems from new services.
Maintain temporary data synchronization mechanisms during the transition period.
Backward Compatibility:
Ensure that the new stateless services can seamlessly interact with existing stateful components.
Provide backward-compatible APIs and data contracts to minimize the impact on dependent systems.
Risk Mitigation
Migrating to a stateless architecture involves inherent risks that need to be mitigated.
Several strategies can help minimize these risks:
Feature Flags:
Implement feature flags to control the rollout of new stateless components.
Enable gradual deployment and testing of stateless services in production environments.
Allow for quick rollback to stateful systems if issues arise.
Fallback Mechanisms:
Maintain fallback mechanisms to revert to stateful systems in case of critical failures.
Ensure that the system can gracefully handle failures and maintain data consistency during the transition.
Challenges with Stateless Services
While stateless services offer numerous advantages such as scalability, fault tolerance, and easier deployment, they also introduce certain challenges that need to be considered and addressed.
Let’s look at a few important challenges:
Increased Network Overhead
One of the primary challenges with stateless services is the increased network overhead:
Context Inclusion: Each request in a stateless system needs to include all the necessary data and context, leading to larger payload sizes.
Frequent Data Retrieval: Without a local state, services may need to frequently retrieve data from external storage, increasing network traffic.
This increased network overhead can impact performance and latency, especially in high-traffic scenarios.
Data Distribution and Consistency
Stateless services often rely on external storage systems for data persistence, which introduces several challenges such as:
Data Replication: Ensuring data consistency across replicated storage systems can be complex.
Partitioning: Efficiently partitioning data across distributed storage while maintaining performance can be challenging.
Eventual Consistency: Dealing with eventual consistency models in distributed systems may require careful design and error handling.
Latency: Accessing external storage introduces additional latency compared to local state access.
Operational Complexity
The distributed nature of stateless architectures can lead to increased operational complexity:
Monitoring: More components and interactions require better monitoring solutions.
Debugging: Tracing issues across distributed services and storage systems can be more challenging.
Infrastructure Costs: Stateless architectures may require additional infrastructure to handle distributed storage and caching.
Data Storage Costs: Storing state in external systems can lead to higher data storage costs.
Organizations need to be prepared to invest in robust operational tools and practices to manage this complexity effectively.
Security Considerations
Stateless services introduce unique security challenges that need to be addressed:
Token Integrity: Maintaining the integrity of authentication tokens becomes crucial in stateless systems.
Secure Communication: Ensuring secure communication channels between services and storage systems is essential.
Data Protection: Protecting sensitive data in transit and at rest across distributed storage requires careful security measures.
Implementing robust security practices and encryption mechanisms is vital to mitigate these risks.
Summary
In this article, we’ve taken a detailed look at stateless architecture and how it can help build more scalable systems.
Let’s summarize the key learnings in brief:
The state is your application's memory—every user session, shopping cart, and authentication token that makes personalized experiences possible.
Modern stateless architectures externalize this state, allowing any server to handle any request, simplifying scaling and improving reliability.
The core principles of stateless architecture are as follows:
Separation of state from logic
Request independency and idempotency
Data consistency models
The advantages of stateless architecture include horizontal scalability, fault tolerance, deployment flexibility, and operational benefits.
In stateless architectures, state management is decentralized from application servers, necessitating thoughtful approaches to storage and access patterns.
Modern stateless architectures employ various communication patterns to maintain system integrity and scalability.
In stateless architectures, authentication flows are designed to be token-based rather than session-based.
The journey from stateful to stateless architecture is best approached through gradual transformation rather than a complete overhaul.
The key challenges with stateless architecture are increased network overhead, data distribution, security considerations, and an increase in operational complexity.